Project Detail
A user’s transactions with modern networks and services produce a vast amount of user related data. The byproduct of
every phone call a person makes or every web page one visits is translated into a log record with usage data. By studying these log
records, the user’s behavior is revealed and one may come up with clues about user preferences, identify security issues, or discover
fraudulent use of the network or the service one provides.
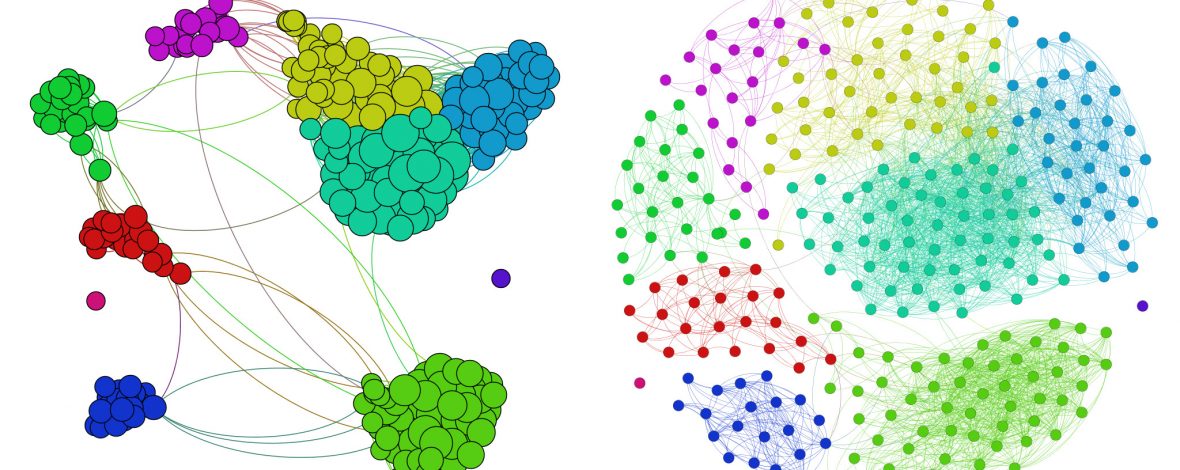
The modeling of network users’ behavior may serve as an invaluable tool for the IT manager. Many of these issues are discussed and emphasis is given on the construction of appropriate
user behavior representation in telecommunications. As an example, the application of two clustering techniques is presented, with the
task to identify appropriate user behavior representations (profiles) inside a large organization’s telecommunications network, in order
to spot fraudulent usage. Through this solutions organization’s network manager may gain more insight into the
problems of user profiling and fraud detection.